
Security Life Cycle
Many people mistakenly believe that information security issues can be solved simply by purchasing security products like firewalls or antivirus software. In reality, information security is a continuous cycle, as shown in the diagram below.
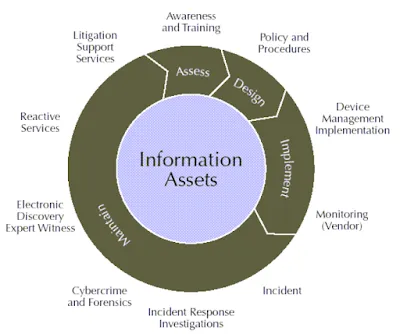
Phase 1: Identifying and Valuing Assets
The first step in any security strategy is determining what you are protecting—your assets. These can be data, applications, or systems. Identifying assets must involve the system owners, as they are the only ones who truly understand the value and importance of each component.
This process is known as an Assessment. Once identified, each asset must be assigned a value. Security investments should generally not exceed the value of the asset itself. For example, if a computer is worth Rp. 5,000,000, it makes no sense to spend Rp. 100,000,000 to secure it; in such cases, having a duplicate might be a better strategy.
In Information Technology, assets are generally categorized into three types:
- Hardware: Physical devices like servers, routers, and disks. Their value often depreciates quickly.
- Software: Applications and systems. Valuing software is more complex, especially for custom-developed or open-source software.
- Data: Often the most difficult to list and value. For example, how much is customer data worth to an online store? Its value might be low to an outsider but critical to the business.
Phase 2: Security Design (Policies and Procedures)
After identifying what to protect, you must design the security framework. This involves developing Policies and Procedures (PnP). Many organizations skip this step and go straight to implementation, which leads to failure. Policies define who can access data and what rules should be applied to authorization and access control.
Phase 3: Technical Implementation
Only after the design is complete should you implement technical security devices. This can be done with the help of specialized vendors to ensure the right technology is used to enforce your policies.
Phase 4: Incident Investigation and Response
Even with the best security, incidents will occur. When they do, they must be investigated to determine if a real breach occurred or if it was a false alarm. Responses are then carried out according to the established policies and procedures.
This completes the Security Life Cycle. Approaching security as a “product” rather than a cycle is like treating a headache with painkillers without ever looking for the underlying cause of the pain.
Security Elements by Category
Information security is not limited to just network security. A comprehensive approach covers multiple layers:
- Computer (Host) Security: Focuses on the security of servers, workstations, and notebooks. This involves managing operating system patches, configurations, and application security.
- Network Security: Addresses risks related to data interception, modification, and Denial of Service (DoS) attacks on the communication architecture.
- Application Security: Even if the host and network are secure, the software itself might have vulnerabilities (e.g., SQL Injection) that allow unauthorized access or data tampering. Database security is also a critical subset of this category.
Author: Budi Raharjo